Three magic words: monitoring, control and modeling.
But if you need more, see below:
It’s a “trend”, that’s exactly what this is, I know because I’ve read it in Forbes, top-shelf authoritative source:
The Internet Of Behavior Is The Next Trend To Watch
Emmanuel Ramos, Forbes Technology Council, Mar 13, 2023
The world of technology is changing rapidly, and with it comes the development of new communication protocols like the Internet of Behavior (IoB). IoB offers a revolutionary way to monitor, control and model human behavior. As tech leaders in this ever-evolving industry, we must stay ahead of upcoming trends so that we can take advantage of its many benefits.
The Internet of Behavior
IoB is a system that uses sensors and other technologies to monitor, analyze and predict human behavior. It combines artificial intelligence (AI), machine learning (ML), big data analytics, cloud computing, Internet of Things (IoT) devices, mobile applications, wearable devices, augmented reality (AR), virtual reality (VR), robotics automation systems and more into one comprehensive platform for collecting behavioral data from individuals or groups. The collected data can then be used for various purposes such as predictive analytics or automated decision-making processes.
The primary benefit of using IoB technology is improved efficiency and productivity gains from automation enabled by predictive analytics. Leveraging AI algorithms for analyzing behavioral patterns in real time can help organizations make better decisions faster while reducing costs associated with manual labor or inefficient processes.
The Internet of Behavior is a rapidly growing technology that has the potential to revolutionize how we interact with and understand our world. In this article, I will explore how IoB works and what technologies are used to implement it.
How IoB Works
IoB is a revolutionary technology that enables the monitoring, control and modeling of human behavior. It combines the power of the technologies mentioned above to provide an unprecedented level of insight into how people interact with their environment. IoB has been used in various industries such as healthcare, retail, finance, education, transportation and more.
Protocols And Ecosystems Involved In IoB
IoB works by connecting devices to each other through networks or protocols like Bluetooth Low Energy (BLE). This connection allows for real-time data exchange between different systems, which can then be analyzed using AI algorithms. Additionally, these connections are often secured using encryption techniques like Transport Layer Security (TLS) to ensure privacy protection. Furthermore, this ecosystem also includes software platforms such as Amazon Web Services or Microsoft Azure which enable organizations to store large amounts of data securely in the cloud while providing scalability options when needed.
Technologies Used To Implement IoB
In order for IoB systems to work effectively, they must utilize several technologies, including sensors that detect changes in environmental conditions, communication protocols such as Wi-Fi or BLE, edge computing capabilities that allow for local processing, ML algorithms that analyze collected data, databases for storing information and APIs that facilitate integration with other applications or services. All these components come together to create an intelligent system capable of understanding user behavior patterns over time so it can make predictions about future actions based on past behaviors.
Challenges Of Developing And Implementing IoB
It is important to understand the protocols and ecosystems involved in IoB, as well as the technologies used to implement it, so you can unlock the potential of this powerful technology for improved efficiency, security and accuracy. Let’s explore further how these advantages can be leveraged with IoB for human behavior monitoring, control and modeling.
Advantages Of Using IoB For Human Behavior Monitoring, Control And Modeling
Automation and predictive analytics enabled by IoB can significantly improve efficiency and productivity gains. For example, IoB systems can be used to automate mundane tasks such as data entry or scheduling appointments, freeing up time for more complex activities that require higher-level thinking skills. Additionally, predictive analytics enabled by IoB can help identify patterns in customer behaviors that may not be immediately apparent to the naked eye.
Enhanced security and privacy protection are other advantages of using IoB for human behavior monitoring, control and modeling. Advanced data encryption techniques are used in these systems, which ensure that sensitive information remains secure at all times while still allowing access only when necessary.
The advantages of using IoB in this way have been demonstrated in terms of improved efficiency and security as well as increased accuracy. As the technology continues to evolve, we will see more sophisticated AI-based solutions emerging and greater emphasis on interoperability standards.
Upcoming Trends In The Development And Use Of IoB Technology
The development and use of IoB technology are rapidly evolving, with new trends emerging in the industry. AI-based solutions are becoming increasingly popular for automated behavioral analysis enabled by this technology. These solutions can help to identify patterns in user behavior that would otherwise be difficult to detect manually. This could include identifying potential security threats or uncovering customer preferences and insights from large datasets. Wearable devices are also gaining traction as an alternative to traditional sensors for collecting behavioral data. They offer a more convenient way of gathering information about user activities without having to install additional hardware or software components on the device itself.
Interoperability standards are also being developed with increasing focus, allowing different platforms utilizing IoB technology to integrate seamlessly across different systems and networks. This will enable users to access data collected from multiple sources within one platform, providing a comprehensive view of their behaviors over time while maintaining privacy and security protocols throughout the process.
Conclusion
In conclusion, the Internet of Behavior is a new communication protocol and ecosystem that promises to revolutionize the way we monitor, control and model human behavior. By leveraging the latest advances in technology such as artificial intelligence and machine learning algorithms, IoB can provide us with unprecedented insights into how people interact with each other and their environment. As this technology continues to evolve, it will become increasingly important for tech leaders to stay abreast of its development so they can leverage its potential benefits for their organizations. – End of Forbes article
Standard PR piece, ChatGPT redacted, I guess…
But damn worrying escalation from the previous piece on the Internet of Bodies and Internet of Things, or about optogenetics!
And we’re not talking about potential for abuse here because this is an abuse technology, abuse is what it does. With no one’s consent.
I didn’t even bother to check with google, but on any other search engine you get a lot of hits for “internet of behavior”, the secret is hidden in the open, as usual. but I leave you with a few of my own findings and resources, and from here there’s no way around knowing your enemy to escape and defeat your enemy.
The most obvious and effective examples of capitalizing on the Internet of Behaviours are Facebook and Google, which display adverts to surfers at frequent intervals depending on the detailed analysis and understanding they have created from consumer behavioral data obtained on a regular basis.
Precedence Research
More so, a Precedence Research report from past year reveals:
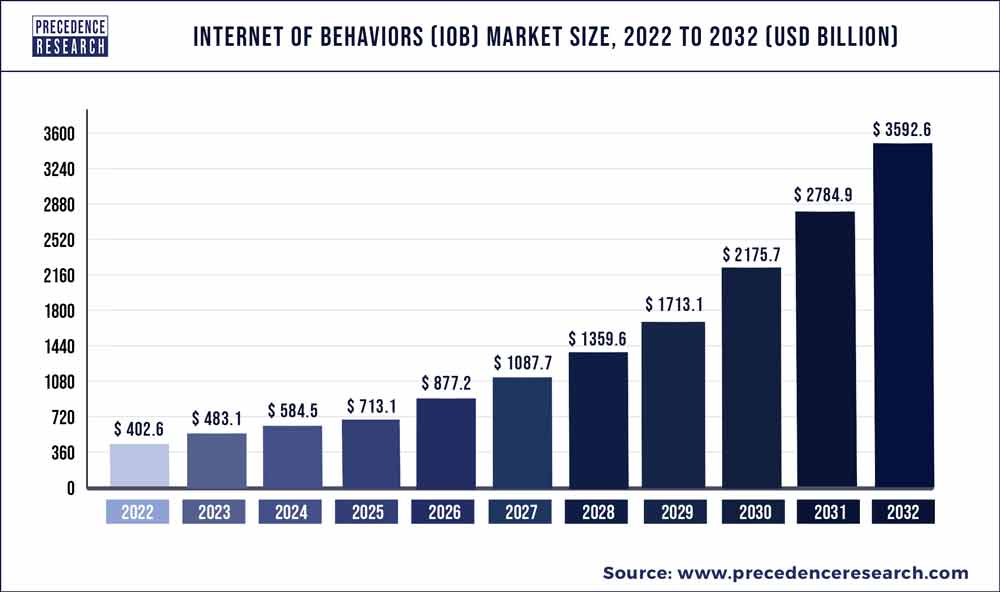
The global internet of behaviors (IoB) market size was valued at USD 402.6 billion in 2022 and is expected to surpass around USD 3592.6 billion by 2032, poised to grow at a compound annual growth rate (CAGR) of 24.97% from 2023 to 2032.
The Internet of Behaviours (IoB) seeks to debate how data may be best understood and is used to build and launch new products from the perspective of human psychology. The IoB may be utilized in a variety of ways by both public and commercial enterprises. This innovation will become an enticing big branding and distribution platform for businesses and organizations all around the world. Every firm gets an in awareness of its clientele, which the IoB platform enables. For instance, IoB links all mobile phones in the program, allowing them to observe their faults and receive visual tips on how to improve their swinging and stroke. The linking of devices generates a large number of new pieces of data and spans beyond the Internet of Things (IoT). Businesses acquire information from customers by ‘sharing’ data amongst linked devices, which are then monitored in real time by a single computer.
While refers to the interconnection of networked physical things that acquire and exchange data over the internet. IoB interprets this data in conjunction with particular human actions ranging from purchasing habits to demographic preferences. Location tracking, big data, and face recognition devices basically map client behavior. Here’s an easy example: Uber. Its Internet of Things app monitors both drivers with passengers. Once the consumer has been left off, Uber polls to assess the ride, allowing the driver’s conduct to be monitored and the quality of customer to be interpreted properly. By 2025, 40% of the world population would be subject to at least 1 IoB program (government or corporate) and digitally tracked in order to affect human behavior. IoB may be a great instrument for leveraging sales and marketing to develop effective strategies that make a difference in the products and services given to customers. But that’s not all; it’s also beneficial to other industries. IoB, for example, is useful in the medical arena, assisting healthcare personnel in assessing individuals’ illnesses, responsiveness to medicines, and other lifestyle information.
Growth factors
Over the last decade or so, there has been an astonishing increase in chronic and weakens the immune system illnesses (NCDs). Every year, over 41 million individuals die as a result of NCDs, resulting in exorbitant healthcare cost. IoB-enabled devices have enabled significant advancements in artificial pancreas technology. According to 2015 research, IoB devices resulted in a 50% reduction in 30-day hospital readmissions. IoB aids in the reduction of automobile insurance premiums. Users can install an app on their phones that collects crucial information such as distance traveled, automobile speed, and time of day the user is driving, and so on. As a result, determine the right premium that the user is entitled to pay. According to the study, prudent drivers would pay minimal rates. Aviva was the first insurance provider to create a smartphone app for tracking driving behavior in 2013.
Several digital advertising firms are already utilizing analytics technologies to gain insights into regular customer habits. Marketers may utilize the Internet of Things to monitor client purchasing behaviors across platforms, gain access to previously unavailable data, reconfigure the value chain, and even bring honest point-of-sale notifications and customized marketing. IoB is regarded as one of the top technology trends for 2021. The COVID-19 epidemic is mostly to blame for IoB becoming a trend since it has revolutionized how consumers engage with brands, forcing businesses to reconsider how they communicate with customers. From the angle of human psychology, the IoB concept attempts to accurately analyze data and use that understanding to build and market new things. The IoB attempts to understand data obtained from users’ online actions from the perspective of behavioral psychology. It seeks to address questions about how to analyze data and how to apply that information to develop and market new products, all from the standpoint of human psychology. This new approach occasionally has an impact on Quality Infrastructure since many organizations might increase their connectivity.
Using IoB technology has assisted numerous firms in reaching out to more clients through internet advertising. Companies may easily identify and target certain individuals or groups to offer their services and goods using the Internet of Behavior. Google and Facebook, for example, both utilize behavioral data to provide relevant adverts to its customers. Companies may use IoB to not only communicate with their target audience, but also track their habits in order to enhance services. Furthermore, new technologies such as Alexa, OK Google, and Siri are designed to study and analyze data and human behavior in order to perform more effectively.
Report Scope of the Internet of Behaviors (IoB) Market
| Report Coverage | Details |
| Market Size in 2023 | USD 483.12 Billion |
| Market Size by 2032 | USD 3592.6 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 24.97% |
| Base Year | 2022 |
| Forecast Period | 2023 to 2032 |
| Segments Covered | Application, Enterprise Size, Industry, Geography |
| Companies Mentioned | Aware Inc., Traceable, Guardian Analytics, Vertica Systems, Trifacta, NuData Security, Mazu Networks Inc., Qubit Digital, Cognitive Scale, Capillary Technologies, Among others. |
Application Insights
Advertising Campaigns, Digital Marketing, Content Delivery, Brand Promotion, and Others are the market segments. Over the projected period, the Digital Marketing sector is likely to occupy a major proportion of the worldwide Internet of Behaviors (IoB) market. Because the internet of behavior (IoB) requires an internet connection, digital marketing services will benefit greatly from IoB technology. Data is the key commodity of digital marketing, which promotes products and services to consumers all over the world. If companies have access to behavioral analysis and interpretation technology, they will be better positioned to engage customers following the purchase process.
In 2022, the digital marketing category is expected to have the highest share. Because an internet connection is required for the internet of behavior (IoB), digital marketing services will benefit the most from IoB technology. Digital marketing is a field that markets products and services to individuals all over the world using data as its primary commodity. They will be in a better position to contact customers at the conclusion of the purchasing process if they have access to tools for behavioral analysis and interpretation. Globally, there is expected to be a major increase in digital marketing. Digital marketing will be used to promote brands, generate leads, and increase sales. The Internet of Business is a big boon to the sales profession. At the same time, for decades, corporations relied on data to make judgments. Why has the IoB trend become so important in today’s commercial, government, and non-profit sectors? First and foremost, IoB focuses on gathering, analyzing, and comprehending user behavior in order to enhance service quality and the value chain. This technology collaborates closely with behavioral science and can provide greater data insights. It also aids in the development of stronger client connections because IoB allows for two-way contact with them. Instead of doing surveys to learn from them, businesses may better understand their consumers’ demands and deliver significant improvements.
Industry Insights
BFSI, Telecom and IT, Media and Entertainment, Tourism & Travel, Retail and e-Commerce, Healthcare, Manufacturing, and Others are the major segments. The BFSI category is expected to occupy a considerable part of the worldwide Internet of Behaviors (IoB) market by 2032. IoB is extensively utilized in the BFSI business for statement generation and automatic notification applications. Brands may maintain an omnichannel presence by swiftly determining a customer’s preferred channels and providing tailored messaging solely through those channels. Consumer connection is being prioritized by financial institutions and retail banks through location-based advertising. These reasons are expected to drive IoB adoption in the BFSI industry.
The most obvious and effective examples of capitalizing on the Internet of Behaviours are Facebook and Google, which display adverts to surfers at frequent intervals depending on the detailed analysis and understanding they have created from consumer behavioral data obtained on a regular basis. However, collecting and analyzing data from IoT is difficult, and many businesses do not have simple access to this data. With the number of IoT devices predicted to triple by 2025, IoT, which has so far had momentum in the B2B industry, is expected to experience rapid acceptance in the consumer segment.
Regional Insights
The adoption of the internet of behaviors in North America is expected to rise at a rapid pace. Furthermore, North America has made significant progress in the use of IoT, particularly in the industrial and automotive industries. Because of the demand for IoT, cloud platforms are seeing widespread acceptance, boosting the growth of the internet of behaviors market throughout the forecast period.
South Asia and the Pacific are expected to emerge as the most opportunistic markets for the internet of behaviors due to the presence of a large consumer population, creating opportunities for organizations engaged in behavioral analytics to better understand consumer behavior and strategize their sales/marketing campaigns accordingly. Furthermore, rising government smart city efforts and cloud investment in the area are expected to fuel market expansion in the near future. Furthermore, the introduction of high-speed networking technologies, increased interest in the area by international firms, and rising demand from developing countries such as India, Indonesia, and Australia are expected to boost market expansion.
Key market developments
Aware, Inc., a major global provider of biometrics software products, solutions, and services, will exhibit its digital identification expertise in many sessions at the Identity Week London 2021 conference, which will be held from September 22 to 23 in London, England. Identity Week London is an ideal venue for Aware to showcase its extensive biometric expertise and solutions for password-less authentication and identity ownership, with a focus on digital identity and complex authentication technologies.
Maxar Technologies’ AFIXTM suite of biometric products was bought by Aware, Inc., a prominent global provider of biometrics software products, solutions, and services, in November 2020. The Aware ABIS product line has expanded with the inclusion of AFIX, which provide turn key also face and fingerprint biometrics matching, in addition forensic analysis softwares for small and medium-sized law enforcement and government organizations.
Key market players
- Aware Inc.
- Traceable
- Guardian Analytics
- Vertica Systems
- Trifacta
- NuData Security
- Mazu Networks Inc.
- Qubit Digital
- Cognitive Scale
- Capillary Technologies
Combined Impact of IoB and IoT
Internet of behaviour is an extension of IoT. Let us try to know more about it. It’s not about the “things” at all when companies use the Internet of Things to persuade us to change our habits. We’ve crossed over into the Internet of Behavior as the IoT connects individuals with their activities.
Consider the IoB as a mash-up of three disciplines:
- Technology
- Analytical data
- Psychology is the study of human behaviour.
Emotions, choices, augmentations, and companionship are the four areas of behavioural science that we examine when we utilize technology.
Companies that know us through the data provided by IoT, can now influence our behaviour using the data provided by IoB. Consider using a smartphone health app to check your nutrition, sleep habits, heart rate, or blood sugar levels. The app can warn you about potentially dangerous circumstances and propose behaviour changes that would lead to a more positive or desirable outcome.
For the time being, corporations are mostly using IoT and IoB to watch and attempt to influence our behaviour to reach Allstate behavior their intended goal—typically, to purchase.
Working of IoB
- How Data Is Collected?
Consumer data may be gathered from a range of sites and technologies, including a company’s website, social media profiles, sensors, telematics, beacons, health monitors (such as Fitbit), and a variety of other devices.
Each of these sites gathers various types of information. For example, a website may keep track of how many times a person visits a certain page or how long they remain on it. Furthermore, telematics may track how hard a vehicle’s driver brakes or the vehicle’s typical speed.
( How is IoT influencing the Human Body?)
- What Happens to the Information Gathered?
Data is collected and analyzed by businesses for a variety of purposes. These reasons include assisting businesses in making educated business decisions, customizing marketing techniques, developing products and services, and driving user experience design, among others.
Companies establish standards to aid in the analysis of this data. When a user performs a specific action(s), the firm then begins to convince the user to modify their behaviour. For instance, if a user visits a company’s page selling men’s slim jeans three times, the digital shop may show them a pop-up ad offering them 25% off a pair of jeans.
- Using Data from a Variety of Sources
Combining data from many sources and evaluating it to make a decision is another component of the Internet of Behaviors. Companies may develop in-depth user profiles for each user by combining data from a variety of sources. These profiles may then be looked at to see what the best course of action is for the person.
For example, on the brand’s Instagram page, a customer called Ted comments on a photo of a new sneaker. Ted visits the brand’s website a few days later and looks at the identical sneaker. After a week, Ted is watching an ad for the sneaker on YouTube. In the meanwhile, the brand is keeping track of all of Ted’s digital content touchpoints.
Because Ted has expressed an interest in the brand’s shoe, the brand may synthesize this information and devise a strategy for converting Ted into a customer. Remarketing display advertising or emailing Ted a discount coupon are examples of actions the brand might do.
Use of IoB in Various Sectors
- IoB in Business
Online advertising is increasingly being used by a variety of businesses to reach out to their clients. They may discover and target certain persons or groups that could benefit from their products or services with the help of IoB.
Both Google and Facebook utilize behavioural data to provide ads to users on their sites. This enables companies to interact with their target consumers and measure their behaviour in response to advertisements via “click rates.”
Similarly, Youtube uses behavioural analytics to enhance the viewer’s experience by only recommending or highlighting videos and subjects that they are interested in.
- IoB During the Covid-19 Pandemic
The epidemic has increased our awareness of the precautions we must take during this period. Employers might use sensors or RFID tags to see if there are any inconsistencies in following safety standards. Restaurants and food delivery applications, for example, utilize the protocol information to guide their decisions.
Swiggy and Zomato, for example, both exhibited and promoted restaurant safety procedures. They also recorded and broadcast the temperature of the delivery person to reassure consumers that they were safe.
- IoB for the Insurance Industry
In the insurance industry, IoB may be quite beneficial. Driver tracking tools are already used by insurance companies like Allstate and StateFarm to track and secure a driver’s conduct. With the help of IoB, they may evaluate the behaviour and perhaps determine if a certain occurrence was an accident or a misjudged assumption on the part of the insured.
This can help prevent incidents of drunk driving, driving under the influence of drugs, and even underage or retired persons from getting behind the wheel and causing an accident.
End-Note
The Internet of Behaviors offers businesses cutting-edge methods for marketing products and services as well as influencing user and employee behaviour. This technology is highly useful to organizations since it allows them to optimize their customer relationships depending on the data acquired.
Behavioral data technology is still developing. However, as new IoT devices proliferate, the argument over what constitutes critical data and ethical use is only beginning.
If it’s about sales and customer service, of course India has been at the forefront of it:
Very related, from our vault:
THE INTERNET OF BODIES AKA THE BORG IS HERE, KLAUS SCHWAB SAYS (BIOHACKING P.5)
Optogenetics and the weaponization of light by the Military BioTech Complex
To be continued?
Our work and existence, as media and people, is funded solely by our most generous supporters. But we’re not really covering our costs so far, and we’re in dire needs to upgrade our equipment, especially for video production.
Help SILVIEW.media survive and grow, please donate here, anything helps. Thank you!
! Articles can always be subject of later editing as a way of perfecting them
! Articles can always be subject of later editing as a way of perfecting them






























:quality(70)/cloudfront-us-east-1.images.arcpublishing.com/mco/2MPMV2TR7BCLTG2AFQ6OBYTEXU.jpg)












 COURTESY OF CHRISTOPHER MOORE / GEORGIA TECH
COURTESY OF CHRISTOPHER MOORE / GEORGIA TECH